Sophos MDR has observed a new campaign that uses targeted phishing to entice the target to download a legitimate remote machine management tool to dump credentials. We believe with moderate confidence that this activity, which we track as STAC 1171, is related to an Iranian threat actor commonly referred to as MuddyWater or TA450.
The first tracked incident was earlier in November, when Sophos endpoint behavioral rules blocked credential dumping activity targeting an organization in Israel. In assessing the activity, we found indicator and TTP overlap with reporting by Proofpoint on TA450. The actor gained initial access through a phishing email directing the user to open a shared document hosted at hxxps[://]ws[.]onehub[.]com/files/ and download a file named ‘New Program ICC LTD.zip’.
The ‘New Program ICC LTD.zip’ archive contained a compressed installer file for legitimate remote monitoring and management (RMM) tool Atera. The Atera installation used a trial account registered to an email address we believe was compromised. Upon installing Atera Agent, the threat actors used Atera remote run commands to execute a PowerShell script (a.ps1) with the goal of dumping credentials and creating a backup file of the SYSTEM registry hive. This credential dumping activity was detected and blocked by Sophos behavioral rules:
“cmdline”: “C:\WINDOWS\system32\reg.exe\” save HKLM\SYSTEM SystemBkup.hiv”
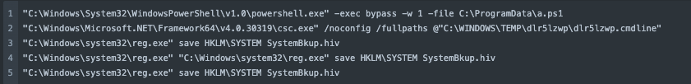
Post-compromise actions in Atera also included:
- Multiple domain enumeration commands;
- An SSH tunnel towards 51.16.209[.]105;
- An obfuscated PowerShell command used to download the Level RMM tool (at hxxps[:]//downloads.level.io/install_windows.exe).
We have seen telemetry of another Sophos non-MDR customer in the United States that follows the same behavior. Sophos X-Ops will continue to monitor this activity and update with any further information on this threat cluster.
Acknowledgements
Sophos X-Ops acknowledges Joshua Rawles, Hristina Ivanova, and Mark Parsons for their work on this threat hunt and contributions to this report.
